With the rise of the Internet of Things (IoT), more and more devices are being connected to the Internet. From smart homes to industrial control systems, IoT devices offer convenience and efficiency. However, the ability to securely access these devices from external networks has become a crucial need. In this article, we’ll discuss how to securely access ssh iot from external network.
Step 1: Configure Your IoT Device for SSH Access
The first step to accessing your IoT device via SSH is to configure your device to allow SSH access. This process varies depending on the device, but it typically involves enabling SSH and setting up a username and password. It’s crucial to use a strong password and to avoid using default login credentials to prevent unauthorized access.
Step 2: Set Up Port Forwarding on Your Router
Once you have configured SSH access on your IoT device, the next step is to set up port forwarding on your router. This involves opening a specific port on your router and forwarding traffic to your IoT device’s IP address. The default port for SSH is 22, but it’s recommended to use a non-standard port for security reasons. For example, you can use port 2222 instead of 22.
Step 3: Use an SSH Client to Access Your IoT Device
After configuring your IoT device and router, you can use an SSH client to access your device. Popular SSH clients include PuTTY, OpenSSH, and SecureCRT. To connect, you’ll need to enter the public IP address of your router, the port number you configured for SSH, and the username and password you set up on your IoT device.
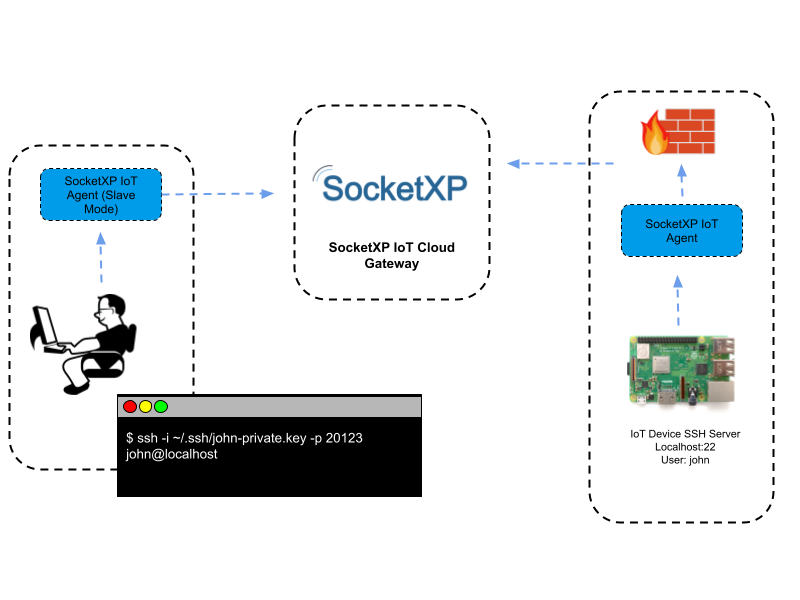
Step 4: Enhance Security with Key-Based Authentication
While using a strong password is a good first step, key-based authentication provides an extra layer of security. With key-based authentication, you use a public key and a private key pair instead of a password to authenticate to your IoT device. This eliminates the need to enter a password every time you connect and makes it much harder for an attacker to gain access to your device.
To set up key-based authentication, you’ll need to generate a public-private key pair using an SSH keygen tool. You’ll then need to copy the public key to your IoT device and configure your SSH client to use the private key for authentication. This way, you can securely access your IoT device without worrying about password-based attacks.
Step 5: Implement Firewall Rules to Secure Your Network
Lastly, it’s essential to implement firewall rules to secure your network. A firewall can be used to restrict incoming and outgoing traffic to your IoT device, preventing unauthorized access. You can configure your firewall to only allow incoming traffic on the port you’ve configured for SSH, and block any other incoming traffic.
Additionally, ssh iot from external network you can set up firewall rules to log any unauthorized attempts to access your device, which can help you detect and respond to potential security threats.
It’s important to note that while SSH provides a secure way to access your IoT devices, it’s not immune to attacks. Malicious actors can still attempt to brute-force passwords, exploit vulnerabilities in your IoT device’s firmware, or intercept traffic between your device and your SSH client.
To mitigate these risks, it’s crucial to keep your firmware up-to-date, use strong passwords or key-based authentication, and monitor your network for suspicious activity. Additionally, you can use a VPN (virtual private network) to encrypt traffic between your device and your SSH client, further enhancing security.
Overall, securing your IoT devices is an essential aspect of IoT implementation. SSH provides a convenient and secure way to access your devices remotely, and by following the steps outlined above, you can ensure that your devices are accessed securely and under your control.
Another aspect to consider when accessing your ssh iot from external network remotely is the potential impact on network performance. Depending on the number and type of devices connected to your network, accessing them remotely via SSH may cause bandwidth limitations or latency issues. In such cases, it may be beneficial to prioritize network traffic or optimize network performance to minimize the impact of remote access on the network.
It’s also worth noting that SSH is not the only way to access your IoT devices remotely. Other options include using a web interface or a remote desktop protocol (RDP). However, these methods may have their own security risks and may require additional setup and configuration.
In summary, remote access to IoT devices is an essential aspect of IoT implementation, and SSH provides a secure and efficient way to achieve this. By following the steps outlined above and considering the potential impact on network performance, you can ensure that your IoT devices are accessible securely and efficiently from external networks.
In conclusion, SSH is an excellent way to securely access your ssh iot from external network. By following the steps outlined above, you can set up SSH access for your IoT device, use key-based authentication and implement firewall rules to enhance security. With these measures in place, you can have peace of mind knowing that your IoT devices are secure and under your control.
















